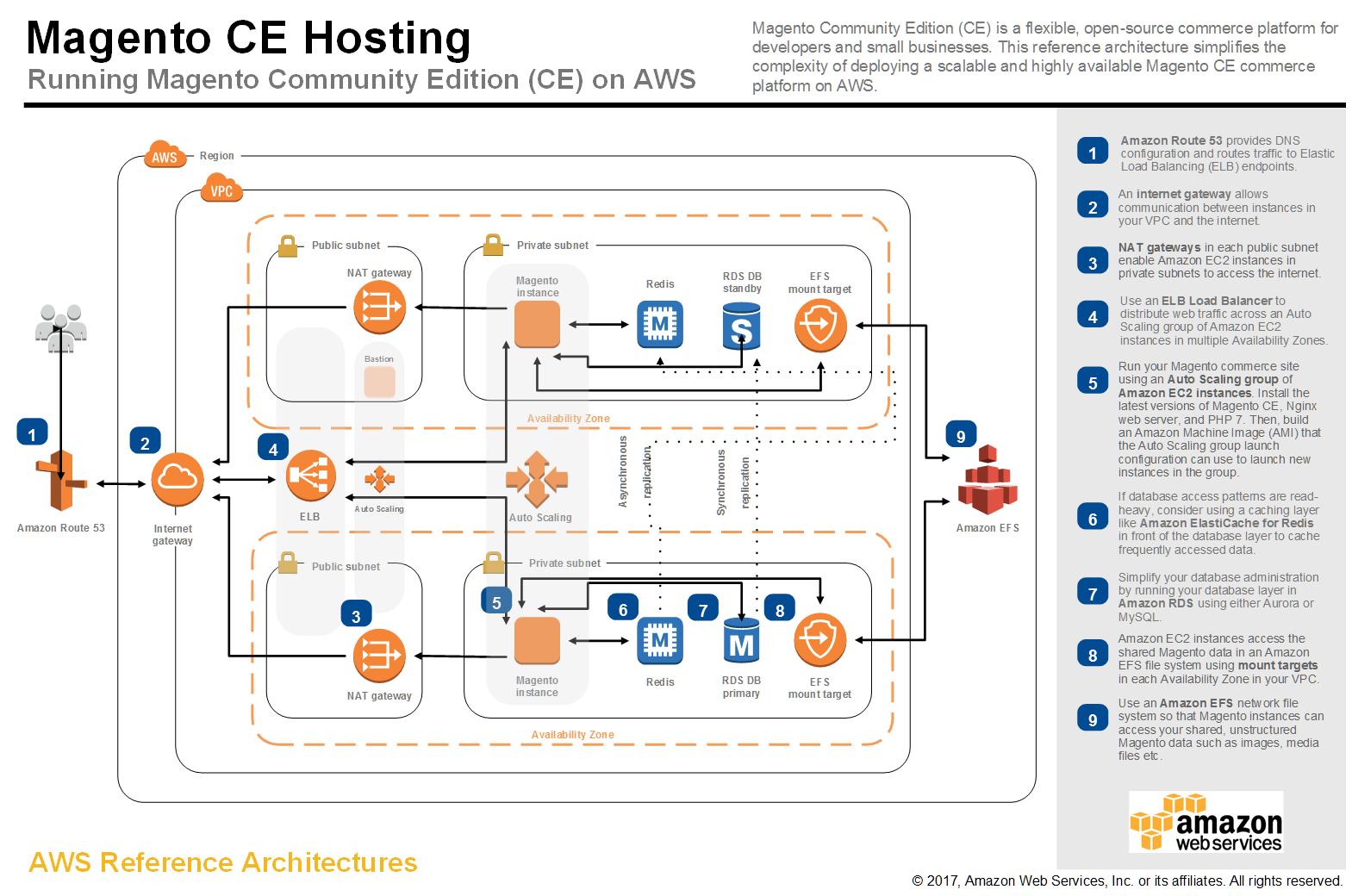
Bastion Host

A bastion host is a special-purpose computer on a network specifically designed and configured to withstand attacks. Asteroids deluxe arcade machine. The computer generally hosts a single application, for example a proxy server, and all other services are removed or limited to reduce the threat to the computer. It is hardened in this manner primarily due to its location and purpose, which is either on the outside of a firewall or in a demilitarized zone (DMZ) and usually involves access from untrusted networks or computers.
Definitions[edit]
The term is generally attributed to a 1990 article discussing firewalls by Marcus J. Ranum. Ranum defined a Bastion host as
The Bastion hosts are used in cloud environments as a server to provide access to a private network from an external network such as the Internet. Since it is exposed to potential attack, a Bastion host must be protected against the chances of penetration.
..a system identified by the firewall administrator as a critical strong point in the network security. Generally, bastion hosts will have some degree of extra attention paid to their security, may undergo regular audits, and may have modified software.[1]
Krutz and Vines have described a bastion host as 'any computer that is fully exposed to attack by being on the public side of the DMZ, unprotected by a firewall or filtering router. Firewalls and routers, anything that provides perimeter access control security can be considered bastion hosts. Other types of bastion hosts can include web, mail, DNS, and FTP servers..Due to their exposure, a great deal of effort must be put into designing and configuring bastion hosts to minimize the chances of penetration.'[2]
In an Amazon Web Services (AWS) context, a bastion host is defined as 'a server whose purpose is to provide access to a private network from an external network, such as the Internet. Because of its exposure to potential attack, a bastion host must minimize the chances of penetration.'[3]. A further AWS related definition is that bastion hosts are 'instances that sit within your public subnet and are typically accessed using SSH or RDP. Once remote connectivity has been established with the bastion host, it then acts as a ‘jump’ server, allowing you to use SSH or RDP to log in to other instances (within private subnets) deeper within your VPC. When properly configured through the use of security groups and Network ACLs (NACLs), the bastion essentially acts as a bridge to your private instances via the internet.'[4]
Placement[edit]
There are two common network configurations that include bastion hosts and their placement. The first requires two firewalls, with bastion hosts sitting between the first 'outside world' firewall, and an inside firewall, in a DMZ. Often smaller networks do not have multiple firewalls, so if only one firewall exists in a network, bastion hosts are commonly placed outside the firewall.[5]
Bastion hosts are related to multi-homed hosts and screened hosts. While a dual-homed host often contains a firewall it is also used to host other services as well. A screened host is a dual-homed host that is dedicated to running the firewall. A bastion server can also be set up using ProxyCommand with OpenSSH.[6]
Examples[edit]
These are several examples of bastion host systems/services:
- DNS (Domain Name System) server
- Email server
- FTP (File Transfer Protocol) server
- VPN (Virtual Private Network) server
See also[edit]
References[edit]
- ^'Thinking about firewalls'. Vtcif.telstra.com.au. 1990-01-20. Retrieved 2012-01-19.
- ^Krutz, Ronald; Vines, Russell (May 2003). The CISM Prep Guide: Mastering the Five Domains of Information Security Management. Wiley. p. 12. ISBN9780471455981.
- ^Malaval, Nicolas (2016-06-14). 'How to Record SSH Sessions Established Through a Bastion Host'. AWS.
- ^Scott, Stuart (2017-12-27). 'Effective security requires close control over your data and resources. Bastion hosts, NAT instances, and VPC peering can help you secure your AWS infrastructure'. Cloud Academy Blog.
- ^'Building a Bastion Host Using HP-UX 11'. windowsecurity.com. 2002-10-16. Retrieved 2016-04-09.
- ^'Using ProxyCommand with OpenSSH and a Bastion server. Chmouel's Blog'. Chmouel.com. 2009-02-08. Retrieved 2012-01-19.
A bastion host is the public face of an internal computer system or network to the Internet and is used to protect sensitive or private data and internal networks. It is one computer or more, depending upon the size of the system and complexity of the security protocols, that is designated as the only host computer that can be addressed directly from a public network. Bastion hosts are designed specifically to screen the remainder of the computer network from being exposed to attack or other breaches of security from the outside. The bastion host is not a general-purpose computer but, instead, it is a special-purpose computer that must be specifically configured to withstand outside attack.Typically, a network administrator will configure a bastion host to have only a single application, such as a server, on the machine, because it is completely exposed to larger distrusted networks such as the Internet. All other applications, unnecessary services, programs, protocols and network ports are removed or disabled in such a way as to lessen threats to the bastion host.
Even with trusted hosts within the computer network, bastion hosts will not share authentication services. This is done so that, even if the bastion is compromised, an intruder will not gain further access into the system that the bastion was designed to protect. In order to be useful, a bastion host has to have some level of access by outside networks but, at the same time, this access makes it especially vulnerable to attack. To minimize vulnerability, hardening is done so that possible ways of attack are limited. A network administrator, as part of the hardening process, will do such things as remove or disable unnecessary user accounts, lock down root or administrator accounts, close ports that aren’t used and configure logging to include when signing onto the server. The operating system will be updated with the latest security updates, and an intrusion detection system also might be run on the bastion host.Bastion hosts are used for such services as mail hubs, web site hosting, file transfer protocol (FTP) servers and firewall gateways.
A network administrator might also use this type of host as a, virtual private network server or domain name Ssystem (DNS) server. Donkey kong country returns online. The name 'bastion' is taken from medieval history. For increased protection, fortresses were built with projections, called bastions, that allowed men to mass behind them and shoot arrows at attackers from a position of greater security.